|
|
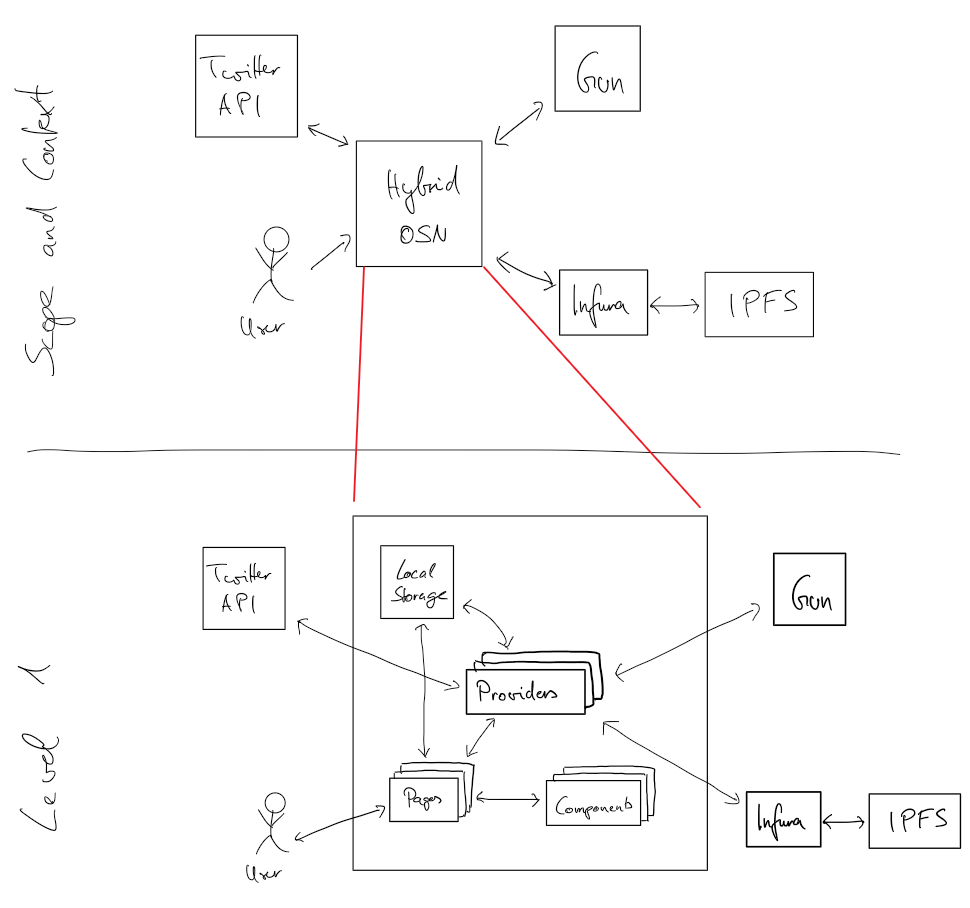
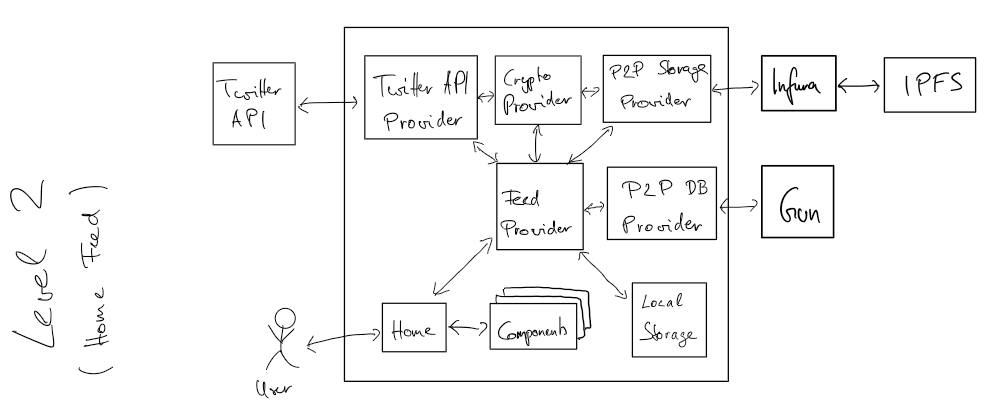
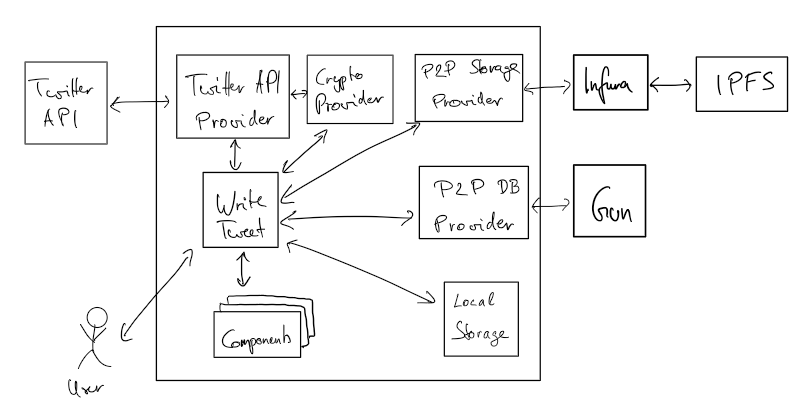
@@ -2,16 +2,32 @@ The software system architecture describes the relationships and properties of i
|
|
|
|
|
|
In the following, the characteristics and peculiarities of the different architectures are described in detail.
|
|
|
|
|
|
+
|
|
|
\begin{figure}[h!]
|
|
|
\centering
|
|
|
- \includegraphics[width=1.0\textwidth]{network-architectures}
|
|
|
+ \begin{subfigure}[c]{0.32\textwidth}
|
|
|
+ \includegraphics[width=\textwidth]{architecture-centralized}
|
|
|
+ \caption{Centralized}
|
|
|
+ \label{fig:architecture-centralized}
|
|
|
+ \end{subfigure}
|
|
|
+ \begin{subfigure}[c]{0.32\textwidth}
|
|
|
+ \includegraphics[width=\textwidth]{architecture-decentralized}
|
|
|
+ \caption{Decentralized}
|
|
|
+ \label{fig:architecture-decentralized}
|
|
|
+ \end{subfigure}
|
|
|
+ \begin{subfigure}[c]{0.32\textwidth}
|
|
|
+ \includegraphics[width=\textwidth]{architecture-distributed}
|
|
|
+ \caption{Distributed}
|
|
|
+ \label{fig:architecture-distributed}
|
|
|
+ \end{subfigure}
|
|
|
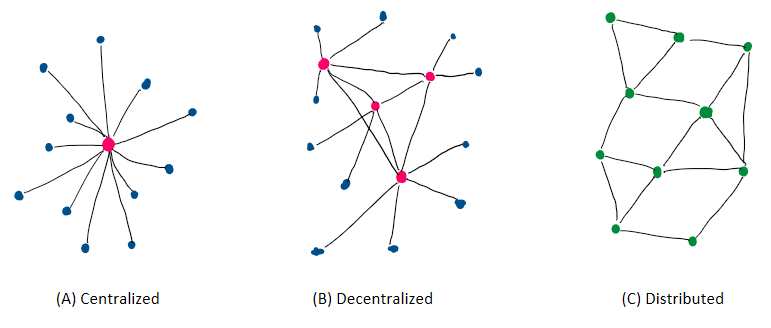
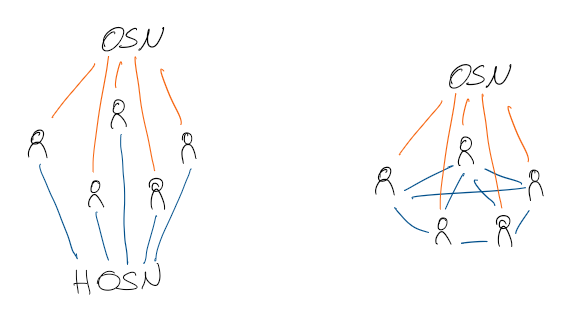
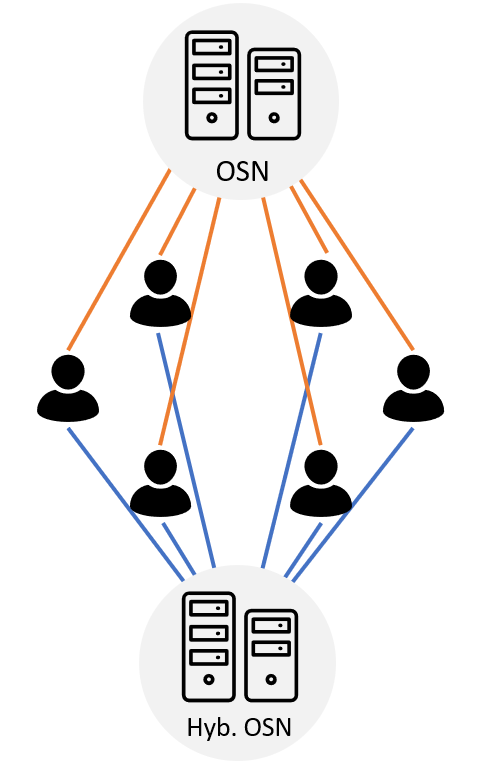
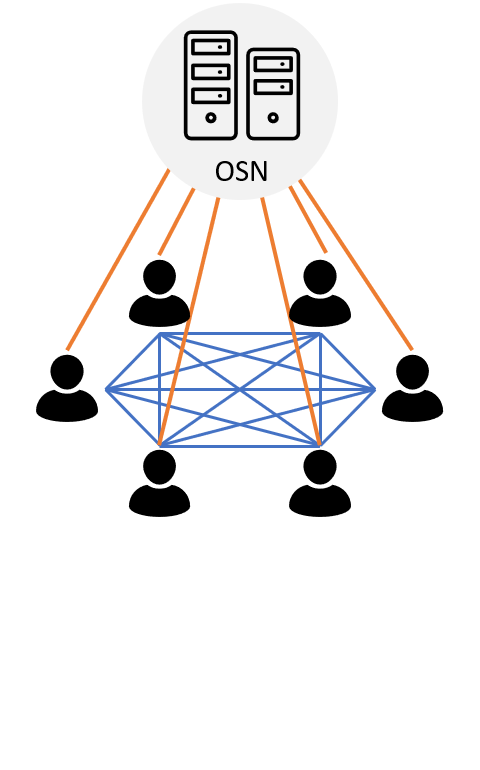
\caption{Schematic representation of various software system architectures. In centralized applications (A), all clients (blue) are in connection with a central server (red), while in decentralized applications (B) several servers provide for improved stability. In distributed applications (C), all nodes have the same role with the same tasks, hence they are called peers (green).}
|
|
|
\label{fig:software-system-architecture}
|
|
|
\end{figure}
|
|
|
|
|
|
+
|
|
|
\subsection{Centralized Applications}
|
|
|
\label{sec:centralized-applications}
|
|
|
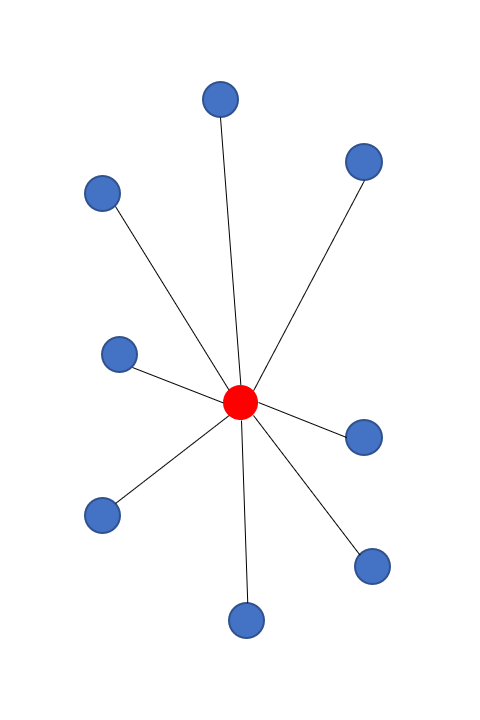
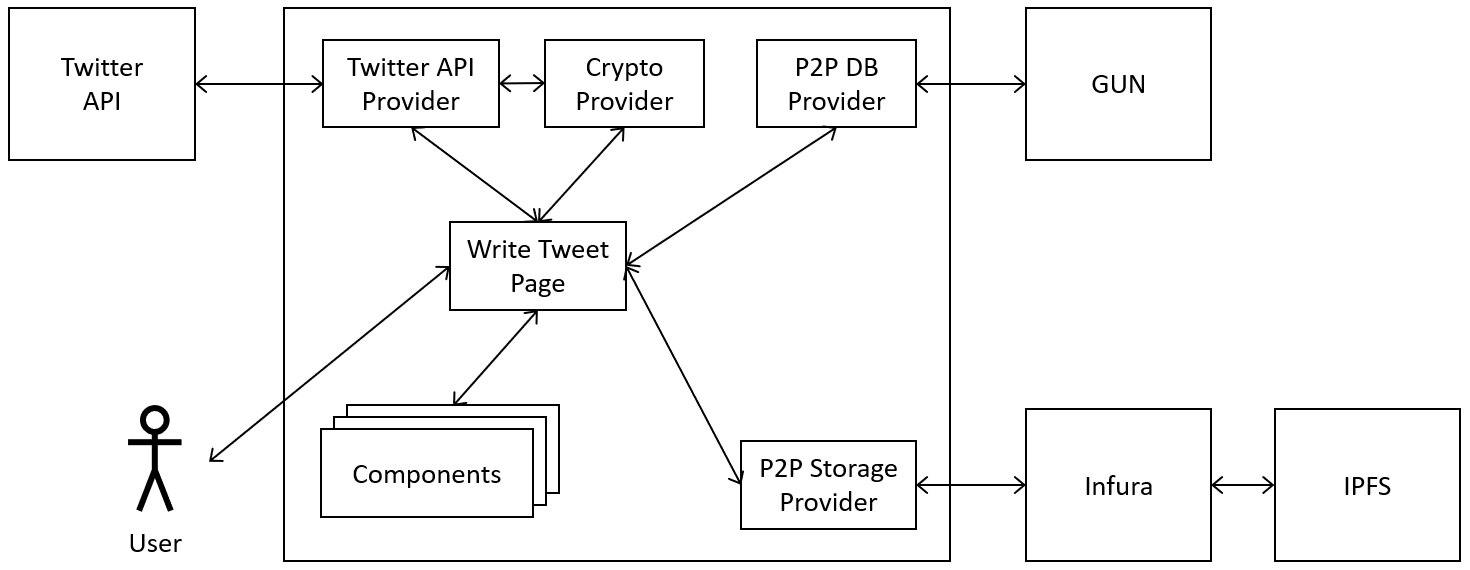
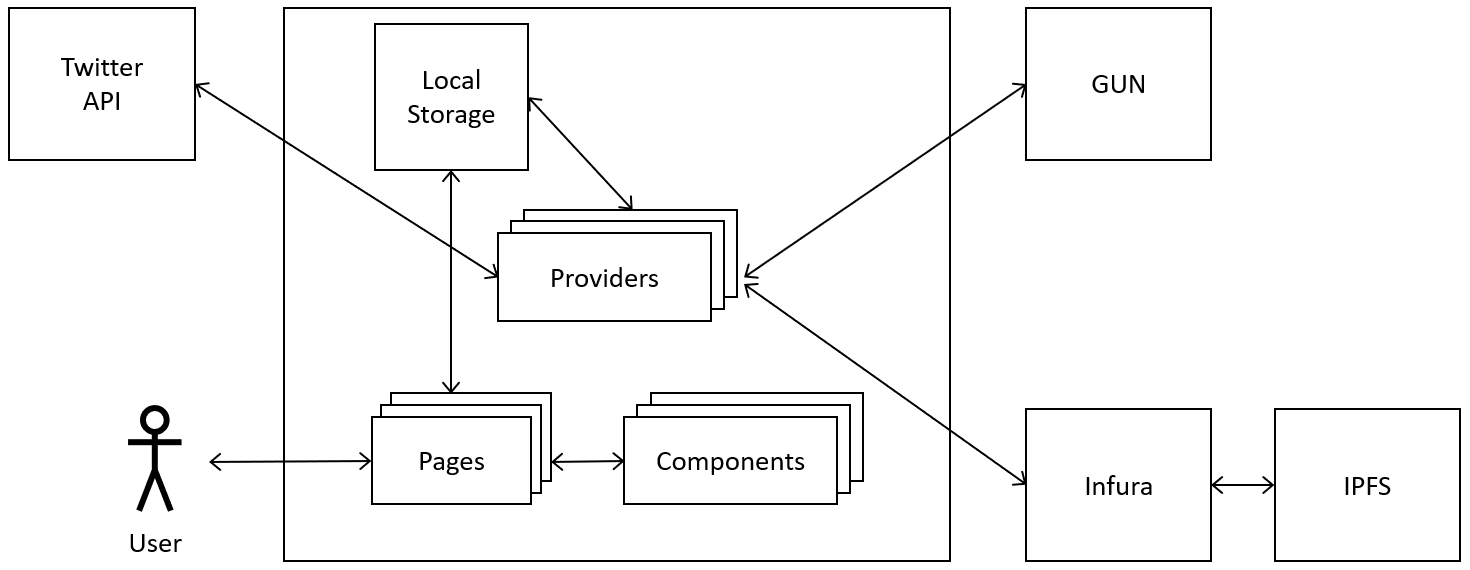
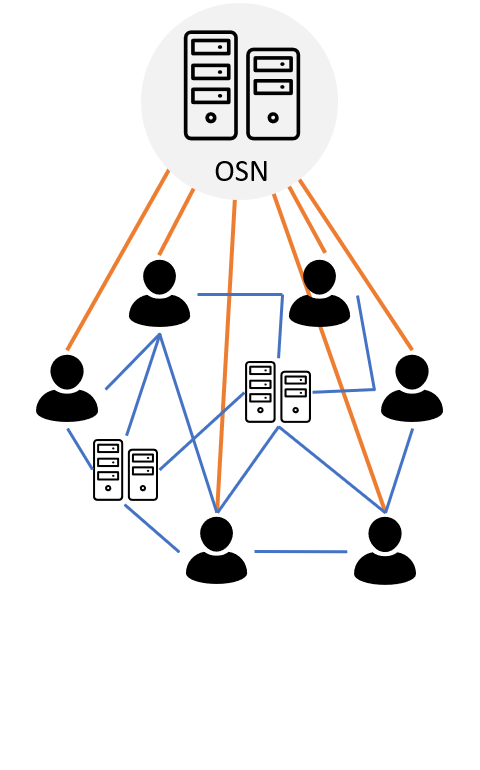
-In a centralized application, the software essentially runs on a central node with a static address with which all other nodes communicate. This central node is called a server and the nodes connected to it are called clients. The clients use the services of the server.
|
|
|
+In a centralized application (see Figure \ref{fig:architecture-centralized}), the software essentially runs on a central node with a static address with which all other nodes communicate. This central node is called a server and the nodes connected to it are called clients. The clients use the services of the server.
|
|
|
|
|
|
Typically, web applications are designed as centralized applications. The clients are usually (mobile) apps or browsers that act as the interface to the user. Examples are social networks such as Facebook and Twitter.
|
|
|
|
|
|
@@ -23,7 +39,7 @@ With regard to web platforms like Facebook, having access to all the data can be
|
|
|
|
|
|
\subsection{Decentralized Applications}
|
|
|
\label{sec:decentralized-applications}
|
|
|
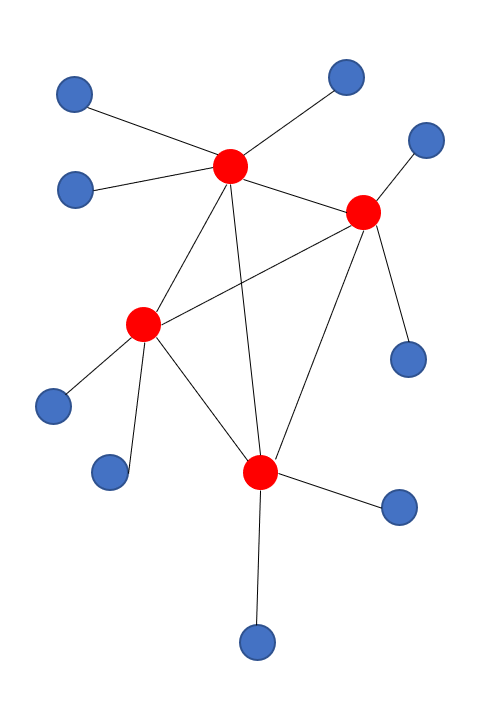
-What are the advantages and disadvantages of centralized applications, is mostly reversed in decentralized systems. Unlike centralized applications, decentralized applications do not have a single point of failure. However, there is no node in the system that has all the data which makes accessing information sometimes hard. There is any number of nodes that perform the tasks of a server and by exchanging with other servers in total form a complete system.
|
|
|
+What are the advantages and disadvantages of centralized applications, is mostly reversed in decentralized systems. Unlike centralized applications, decentralized applications do not have a single point of failure (see Figure \ref{fig:architecture-decentralized}). However, there is no node in the system that has all the data which makes accessing information sometimes hard. There is any number of nodes that perform the tasks of a server and by exchanging with other servers in total form a complete system.
|
|
|
|
|
|
Another advantage is that each server only handles the number of users covered by its resources. New servers contribute additional resources to the overall system. Distributed applications cannot be disabled easily because a new server can be started at any time that does not fall under a lock. Because the data are not centrally available, they cannot be processed, so that user data are better protected. Also, there is no longer a prominent attack target. So, hacking a single server loses lucrativeness.
|
|
|
|
|
|
@@ -33,7 +49,7 @@ Examples of decentralized applications are the social networks diaspora* and Mas
|
|
|
|
|
|
\subsection{Distributed Applications}
|
|
|
\label{sec:distributed-applications}
|
|
|
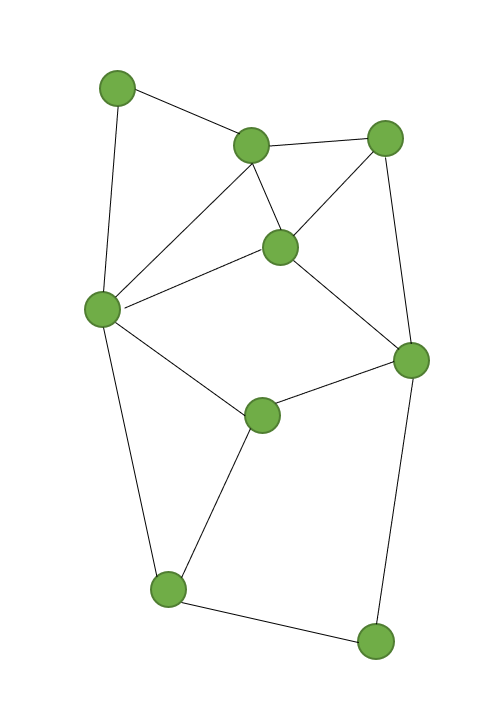
-A feature of distributed applications is the computation across all nodes. At the same time, a single task is executed in parallel on several nodes of a system, and the entire system delivers the result in total. The boundaries between decentralized and distributed networks are becoming blurred. A decentralized network consisting only of servers corresponds quasi to a distributed network.
|
|
|
+A feature of distributed applications is the computation across all nodes (see Figure \ref{fig:architecture-distributed}). At the same time, a single task is executed in parallel on several nodes of a system, and the entire system delivers the result in total. The boundaries between decentralized and distributed networks are becoming blurred. A decentralized network consisting only of servers corresponds quasi to a distributed network.
|
|
|
|
|
|
In distributed applications, there is no hierarchy with servers or clients. Each node is equal to the other nodes with everyone performing the same tasks. For this reason, a node in this architecture is called a peer. The structure is then referred to as \ac{P2P}. With such structures, there are no scaling problems, since each node contributes the required resources itself. Thus, the resources of the entire system grow with each new node added.
|
|
|
|