|
|
@@ -1,44 +1,31 @@
|
|
|
-\chapter{Concept}
|
|
|
+\chapter{Concept of a Hybrid Online Social Network}
|
|
|
\label{ch:concept}
|
|
|
+\input{content/04-concept/introduction}
|
|
|
|
|
|
-The last few years have shown that the private data of users in social networks is not secure. On the one hand, social networks are popular targets for hackers and on the other hand, the collected personal data is processed and used, for example, for targeted advertising. For the users of the network it is easy to share personal information, messages and pictures with other users. While the circle of users who can see this data can usually be determined by the author himself, the social network inevitably has access to this data because it is stored on the operator's servers. What happens to the data is not transparent to the user. But there are also social networks like Ello\footnote{https://ello.co/} or Vero\footnote{https://www.vero.co/} that make it their business to protect users' data in a special way and promise to take care. Unfortunately, such networks fail regularly because the users of the large social networks are trapped on these platforms by a lock-in effect. Since the majority of contacts on the large networks are already linked, it is unattractive to switch to a smaller, new social network where the contacts are missing.
|
|
|
+\section{Requirements to the Hybrid OSN}
|
|
|
+\label{sec:requirements}
|
|
|
+\input{content/04-concept/requirements}
|
|
|
|
|
|
-Users are faced with the dilemma that switching to another social network entails the loss of contacts they have collected over years. But staying with the large network entails uncertainty about their own data. So, the question is how to share fewer sensitive data with the provider, despite the usual use of a social network. In the context of this master thesis, this question was dealt with intensively and a solution of a hybrid social network was worked out. The idea of a hybrid OSN was initially proposed by researchers of the Researcher Training Group (RTG) \enquote{2050 - Privacy and Trust for Mobile Users}\footnote{https://www.informatik.tu-darmstadt.de/privacy-trust/privacy\_and\_trust/index.en.jsp}.
|
|
|
+\section{Stakeholders}
|
|
|
+\label{sec:stakeholders}
|
|
|
+\input{content/04-concept/stakeholders}
|
|
|
|
|
|
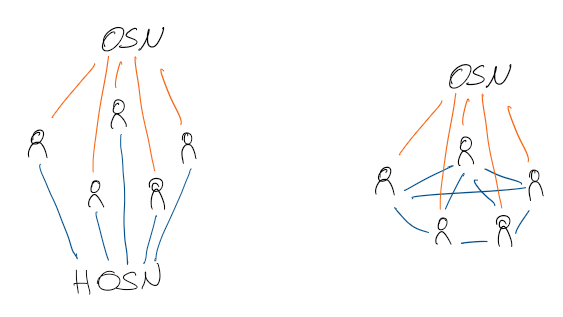
-\enquote{Hybrid} in this case means that an existing (social) network is extended by another network for data exchange. This is a P2P network among the users of the social network, which allows data to be exchanged directly so that the operator of the social network is not aware of it. When using the social network, the P2P network is to be superimposed like a privacy layer. During the actions carried out, the user can then decide for himself via which network the data should be exchanged. In order to exchange data via a P2P network, the usual client must be extended or manipulated for the respective social network or a separate client must be developed for use. Using a P2P network would also have the advantage that the data could not be censored by the operator of the OSN.
|
|
|
+\section{Restrictions}
|
|
|
+\label{sec:restrictions}
|
|
|
+\input{content/04-concept/restrictions}
|
|
|
|
|
|
-The following sections describe the requirements for the respective components OSN, P2P network and client.
|
|
|
+\section{Quality Goals}
|
|
|
+\label{sec:quality-goals}
|
|
|
+\input{content/04-concept/quality-goals}
|
|
|
|
|
|
-\section{Requirements to the OSN}
|
|
|
-\label{sec:requirements-osn}
|
|
|
+\section{Solution Strategy - Architecture}
|
|
|
+\label{sec:solution-strategy-architecture}
|
|
|
+\input{content/04-concept/solution-strategy-architecture}
|
|
|
|
|
|
-Social networks are usually used via a web frontend or associated apps. While there is no way to influence the content and extend the functionality of apps, web pages can be manipulated by browser add-ons to add the desired functionality. Another possibility is to display the contents of the social network in a separate, self-developed application. In this case one would have complete control and could adapt the functionalities accordingly. There are two possible ways to access the original content of the social network. First, the websites could be crawled and the content extracted. Second, some social networks provide interfaces that allow developers to communicate directly with the servers and thus exchange data easily. These interfaces are called API.
|
|
|
-
|
|
|
-Most of the social networks offer an sort of API. But in most cases, the APIs provide only a very limited scope of functionality of the network. Often it is only possible to include public content into a website, like Tweets are often embedded on news websites. Not only the amount of functionality is limited, the number of requests per time interval is often limited, too. Crawling in contrast does not rely on the service provider. A clear advantage is that this way always works. However, much more effort is needed to extract the desired data from the website. The data is expected in a certain structure in order to be extracted. If this structure is changed by the operator of the social network, the crawling fails and the data can no longer be extracted. In addition, social networks today are complicated web applications. The content is dynamically reloaded and the page changes dynamically depending on the action. This is difficult to capture with crawlers. Furthermore, networks protect themselves from crawlers and try to prevent them from crawling content. In the best case, the network operator does not notice that his page is being crawled because ideally the crawler behaves like a normal user and can therefore not be distinguished. To publish content in the social network, the requests sent to the network would have to look as if they had been created by the forms in the web frontend. Here, too, various security mechanisms attempt to identify and block such \enquote{faked} requests, as this could also be used to load malicious code onto the servers. All in all, it is very difficult nowadays to communicate with the servers of a social network via crawling and fake requests.
|
|
|
-
|
|
|
-It is much easier if an interface is provided and clearly documented how data can be retrieved or added. It is important that the essential functions are provided via the API, so that a client application can be developed that is not inferior to the original website in terms of functionality. Otherwise the users won’t switch to the alternative client. By using an API, one enters into a certain dependency on the network. There is no guarantee that the provider will keep up the API and offer all the functionality. Since they are the provider, they decide what happens to the API and the developers using the API and build their applications are completely dependent on them.
|
|
|
-
|
|
|
-To use an API, usually a previous registration is necessary. After registration, the developer receives an API key, which is sent with every request to the API and checked for validity. The number of negative incidents with different social networks has led to providers gradually restricting their APIs more and more. One is the removal of endpoints for certain actions, the other is the introduction of limits. By sending the API key, it is possible to see which developer or which application communicates with the API. Limits can then be used to determine how many requests are processed in a certain time interval or how many users can use the network via this application. It is also possible that the developer has to pay for the API key.
|
|
|
-
|
|
|
-Regardless of the method chosen to exchange data with the social network, a unique content identifier is required. This is necessary so that interactions with it can be related. By knowing the ID of a post, associated comments can be loaded - both from the provider's server and from the private P2P network.
|
|
|
-
|
|
|
-\section{Requirements to the Hybrid Client}
|
|
|
-\label{sec:requirements-client}
|
|
|
-
|
|
|
-In order for users to be ready to use an alternative hybrid client for social networking, this client must meet a number of requirements. First, all the functionality that the user knows from the official app/website must be available. If this is not the case, they will always be forced to go back to the original application. Using more than one app for a network is not user friendly and should be avoided. Basically, great importance should be given to user-friendliness. Complicated procedures should be avoided as best as possible or simplified in such a way that really every user is able to understand and use them correctly. This also means that great importance must be attached to a good user experience, so that content is presented in an appealing way and operation is intuitive.
|
|
|
-
|
|
|
-The hybrid client must also meet a number of technical requirements in order to be accepted by the user and contribute to a good user experience. This includes, among other things, the availability for common operating systems. It is necessary that the hybrid client can be used wherever the social network can otherwise be used. If messages are exchanged via the P2P network, but there is no client for Apple’s iOs, for example, users with an iPhone cannot retrieve this message on the move. This would result in the message being exchanged via the OSN's server despite the sensitive content that is to be protected from the OSN's operator, since only in this case can the recipient receive the message. It is also important that the hybrid client uses resources such as memory, battery and data volume sparingly. Since client devices (peers) play a special role in a P2P network, the careful use of resources is particularly challenging. This is because the data must be stored on the peers and ideally made available to other peers at any time. It should also be possible for a user to log on to several devices with his account and still benefit from all the advantages. This parallel use and the synchronicity of the data must be guaranteed.
|
|
|
-
|
|
|
-Finally, the security of the data exchanged between the hybrid clients must be guaranteed. The OSN must not be able to use these data and even less not be able to assign these data to a certain user. It must also be ensured that the data can only be read by those users who are authorized to do so. These security aspects must have the highest priority when designing the system.
|
|
|
-
|
|
|
-Most social networks can be used free of charge. Ideally, the use of the hybrid client is also free. Otherwise it could be the first argument against using this client.
|
|
|
-
|
|
|
-\section{Requirements from the OSN}
|
|
|
-\label{sec:requirements-from-osn}
|
|
|
-
|
|
|
-Basically it can be assumed that the operator of an OSN does not like the idea of a P2P extension of his network. Therefore, information from the P2P network should be offered to the operator without establishing a reference to a user. With this anonymous data, the operator still has important information at his disposal, for example for the recognition of trends.
|
|
|
+\section{Solution Strategy - Client}
|
|
|
+\label{sec:solution-strategy-client}
|
|
|
+\input{content/04-concept/solution-strategy-client}
|
|
|
|
|
|
\section{Summary}
|
|
|
\label{sec:concept-summary}
|
|
|
-
|
|
|
-\textit{todo...}
|
|
|
+\input{content/04-concept/summary}
|